Google Kubernetes Engine Status. Is Google Kubernetes Engine Down?
Check if Google Kubernetes Engine is down, official outages, user-reported issues, and outages map.
Is Google Kubernetes Engine down right now?
Google Kubernetes Engine is working normally
Google Kubernetes Engine service health. Issues reported in the last 24 hours
Check the number of user-reported issues over the past 24 hours, grouped into 20-minute intervals. It's normal to see occasional reports, which may be due to individual user issues rather than a broader problem. We only consider an issue widespread if there are multiple reports within a short timeframe.
Be the first to know when Google Kubernetes Engine goes down
One place to monitor all your cloud vendors.
Get instant alerts when an outage is detected.
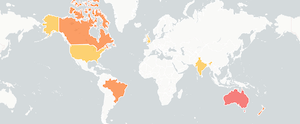
User reports for Google Kubernetes Engine
See what users are saying about Google Kubernetes Engine issues that impacted them and how they are affected by the outage.
-
Gaurav - I am unable to open the Kubernetes documentation page; it returns a 404 error. How can I fix this?.
Google Kubernetes Engine outages and downtime history
IsDown has tracked 50 incidents for Google Kubernetes Engine since started monitoring Google Cloud status in July 2020. We collect data from 5350+ services, and normalize the data to give you a clear picture of the impact of the outage. It will show official Google Kubernetes Engine outages and also issues that we're started by a spike in crowdsource reports.
| Date | Incident | Duration |
|---|---|---|
|
Jul 18, 2025
03:54 PM UTC
|
Minor
We're currently experiencing elevated latency and error rates for several Cloud services in the u...
|
about 2 hours |
|
May 20, 2025
11:07 AM UTC
|
Minor
Description:
We are experiencing an issue with Google Compute Engine, Google Kubernetes Engine, C...
|
about 1 hour |
|
Mar 30, 2025
01:30 AM UTC
|
Major
Customers are experiencing connectivity issues with multiple Google Cloud services in zone us-eas...
Our engineers are actively working on recovery following a power event in the affected zone. Full...
|
about 1 hour |
|
Nov 16, 2024
10:13 AM UTC
|
Major
Multiple GCP Products including Google Cloud Networking, Virtual Private Cloud (VPC), Cloud Load ...
Summary: Multiple GCP Products including Google Cloud Networking, Virtual Private Cloud (VPC), Cl...
|
about 2 hours |
|
Oct 30, 2024
12:17 AM UTC
|
Minor
Summary: Multiple GCP products impacted in australia-southeast2
Description: We are experiencing ...
|
about 2 hours |
|
Oct 24, 2024
02:56 AM UTC
|
Major
Summary: Multiple GCP services impacted in europe-west3-c zone
Description: We are experiencing a...
|
about 6 hours |
|
Aug 03, 2024
11:36 AM UTC
|
Major
Summary: Multiple product outage in europe-west9-a
Description: We are experiencing an issue in e...
|
about 2 hours |
|
Jul 15, 2024
05:44 PM UTC
|
Major
Summary: us-central1: Multiple Cloud Products Experiencing Elevated Errors and Degraded Query Per...
|
about 1 hour |
|
May 16, 2024
11:24 PM UTC
|
Major
Multiple cloud products are experiencing network connectivity issues. New instances of several cl...
Summary: Programming failures for New Virtual Private Cloud endpoints globally affecting New GCE ...
|
about 2 hours |
|
Mar 28, 2024
05:35 PM UTC
|
Minor
Summary: Cloud Customers may experience minimal service disruption in us-east5-c
Description: We ...
|
about 1 hour |
Be the first to know when Google Kubernetes Engine goes down
One place to monitor all your cloud vendors.
Get instant alerts when an outage is detected.
Google Kubernetes Engine components or services current status
| Component | Status |
|---|---|
| Google Kubernetes Engine (asia-east1) | OK |
| Google Kubernetes Engine (asia-east2) | OK |
| Google Kubernetes Engine (asia-northeast1) | OK |
| Google Kubernetes Engine (asia-northeast2) | OK |
| Google Kubernetes Engine (asia-northeast3) | OK |
| Google Kubernetes Engine (asia-south1) | OK |
| Google Kubernetes Engine (asia-south2) | OK |
| Google Kubernetes Engine (asia-southeast1) | OK |
| Google Kubernetes Engine (asia-southeast2) | OK |
| Google Kubernetes Engine (australia-southeast1) | OK |
| Google Kubernetes Engine (australia-southeast2) | OK |
| Google Kubernetes Engine (europe-central2) | OK |
| Google Kubernetes Engine (europe-north1) | OK |
| Google Kubernetes Engine (europe-southwest1) | OK |
| Google Kubernetes Engine (europe-west1) | OK |
| Google Kubernetes Engine (europe-west10) | OK |
| Google Kubernetes Engine (europe-west12) | OK |
| Google Kubernetes Engine (europe-west2) | OK |