Is AWS Down? AWS Status & Outages
AWS status updated
What is AWS status right now?
AWS is having a minor outage
AWS service health over the last 24 hours
This chart shows the number of user-reported issues for AWS service health over the past 24 hours, grouped into 20-minute intervals. It's normal to see occasional reports, which may be due to individual user issues rather than a broader problem.
Outage Map
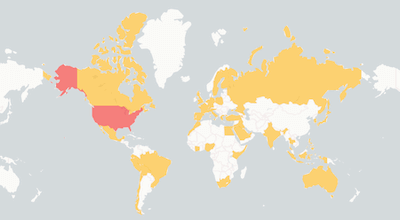
See where users report AWS is down. The map shows recent AWS outages from around the world.
Top locations, last 24h:
- United States
- Canada
Recent AWS outage reports
See what users report when AWS is down and how AWS outages affect them.
-
🇺🇸 United States of America
some pipeline stage get stuck. some fail.
AWS CodeBuild -
🇨🇦 Canada
EC2 instance cant reach ECR in ca-central-1.
Amazon Elastic Container Registry -
🇺🇸 United States of America
Images from s3 bucket not displaying on my site.
-
🇮🇳 India
My DBeaver uses Amazon Redshift and it is unable to load my database..
Amazon Redshift -
🇭🇰 Hong Kong
Tester - AWS Bedrock keeps popping "Failed to fetch" banners in console.
-
🇺🇸 United States of America
Can't access Sleep Number website due to CloudFront issues..
Amazon CloudFront -
🇮🇪 Ireland
Adam - Analysis are crashing, cannot add values to charts, Browser console is full of errors "Uncaught TypeError: Cannot read properties of null (reading 'filter')".
AWS QuickSight -
🇺🇸 United States of America
Tracye - AWS isn’t working…I’m getting the cute dog photo and can’t buy anything on amazon.
-
🇺🇸 United States of America
Cannot order from Amazon..
-
🇪🇨 Ecuador
Alex - i cant see price or articules.
-
🇺🇸 United States of America
Amazon will not list everything..
-
🇧🇷 Brazil
All links to files in cloudfront.net returns `DNS_PROBE_FINISHED_NXDOMAIN` error..
Amazon CloudFront -
🇺🇸 United States of America
using sagemaker for ProQuest TDM studio app through UW Madison, not connecting: "us-east-1.console.aws.amazon.com took too long to respond".
Amazon SageMaker -
🇮🇹 Italy
Andrea - Roblox Studio crashes on startup and fails to get HttpQueryInfo from s3.amazonaws.com/setup.roblox.com/.
-
🇫🇮 Finland
Aliaksei - me-central-1 eks is not responding.
Early detection is everything
AWS Downtime Health — Last 90 Days
In the last 90 days, AWS had 14 incidents with a median duration of 1 hour 36 minutes.
Incidents
Major Outages
Minor Incidents
Median Resolution
Recent AWS outages detected by IsDown
Full incident reports for recent AWS outages, including timelines, affected components, and resolution details.
| Title | Started At | Duration |
|---|---|---|
|
We are investigating increased error rates in the EU-CENTRAL-2 Region.
|
Mar 07, 2026 at 07:53 PM UTC
|
about 1 hour |
|
We are investigating increased API error rates in a single Availability Zone (mes1-az2) in the ME...
|
Mar 02, 2026 at 05:56 AM UTC
|
Ongoing |
|
We are investigating issues with AWS services in the ME-CENTRAL-1 Region.
|
Mar 01, 2026 at 12:51 PM UTC
|
Ongoing |
|
We are experiencing intermittent missing or delayed EC2 instance and status check metrics in the ...
|
Feb 25, 2026 at 06:14 PM UTC
|
about 3 hours |
|
We are investigating connectivity issues impacting AWS Direct Connect connectivity to the US-EAST...
|
Feb 21, 2026 at 12:38 AM UTC
|
about 2 hours |
|
We are investigating connectivity loss impacting AWS Direct Connect connectivity to the US-EAST-1...
|
Feb 21, 2026 at 12:38 AM UTC
|
30 minutes |
|
Possible Outage Indicated by User Reports
|
Feb 18, 2026 at 01:24 AM UTC
Never acknowledged
|
about 2 hours |
|
Possible Outage Indicated by User Reports
|
Feb 16, 2026 at 02:27 PM UTC
Never acknowledged
|
31 minutes |
|
We are investigating DNS resolution failures for some specific CloudFront distributions. We are a...
|
Feb 10, 2026 at 09:15 PM UTC
|
about 7 hours |
|
We are investigating DNS resolution failures for some specific CloudFront distributions. We are a...
|
Feb 10, 2026 at 08:51 PM UTC
IsDown detected 23 minutes before official update
|
about 1 hour |
AWS Components Status
Check if any AWS component is down. View the current status of 269 services and regions.
Compare AWS vs alternatives
Compare AWS status, outages, and service health against alternatives. See which services go down less often.
Stop wasting hours on 'is it us or them?'
- Check multiple status pages
- Hear about outages from your customers
- Wonder "is it us or them?"
IsDown monitors AWS status and all your dependencies to alert you when something goes wrong.
Start 14-day free trialTrusted by 500+ teams · No credit card required
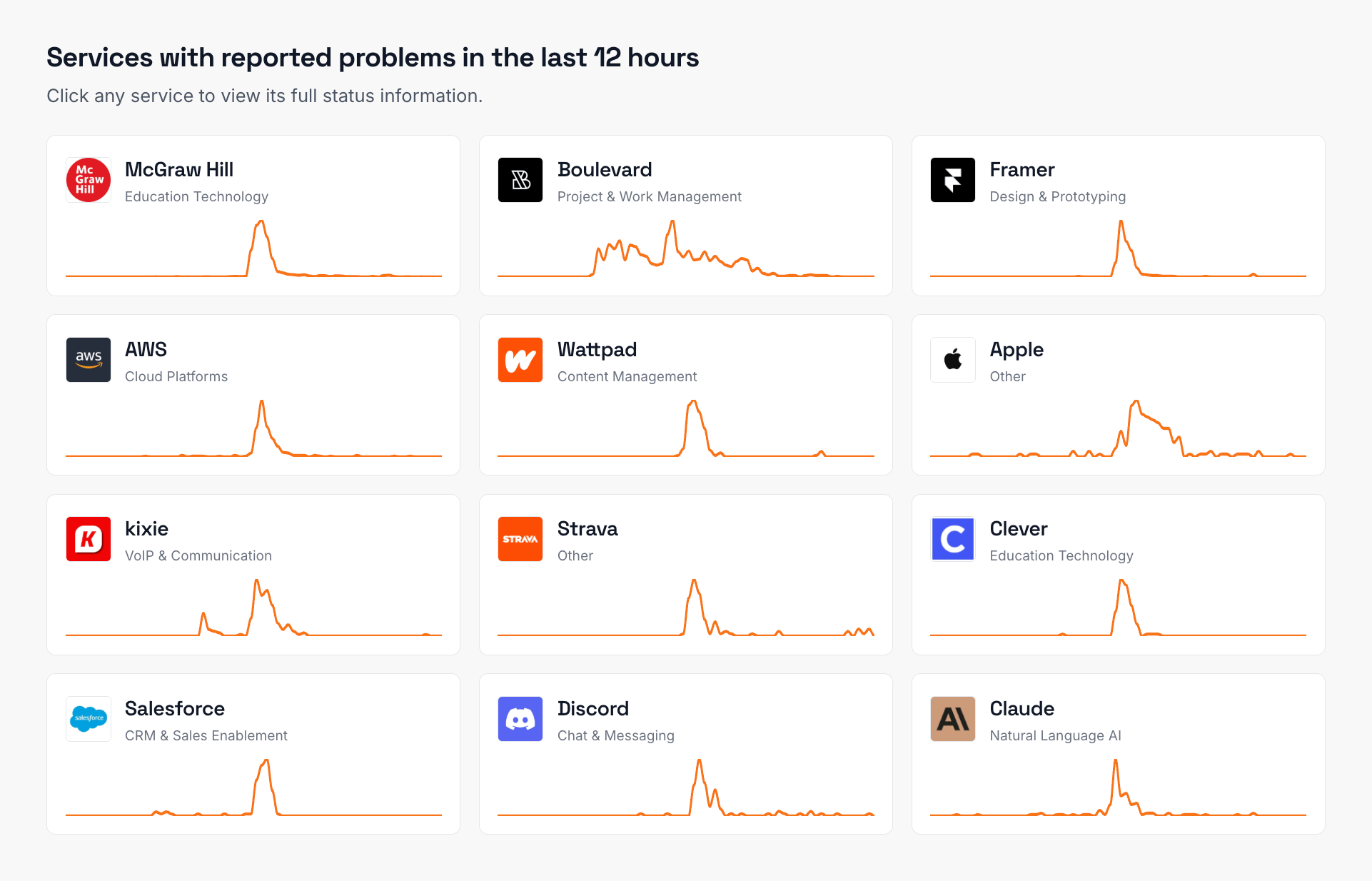
Monitor AWS alongside these services
Teams that track AWS status also keep an eye on these services. Add them all to your IsDown dashboard for a single view of your dependencies.















About AWS Status and Outage Monitoring
IsDown has monitored AWS continuously since May 2020, tracking this Cloud Platforms for 6 years. Over that time, we've documented 389 outages and incidents, averaging 5.6 per month. When AWS goes down, incidents typically resolve within 143 minutes based on historical data.
We monitor AWS's official status page across 5,228 components organized into 269 groups. IsDown interprets AWS statuses (operational, informational, degraded, and disruption) to deliver precise health metrics and filter alerts by the components you actually use.
To check if AWS is down, IsDown combines official status data with user reports for early detection. Vendors often delay acknowledging problems, so user reports help us alert you before the official announcement.
Engineering and operations teams rely on IsDown to track AWS status and receive verified outage alerts through Slack, Teams, PagerDuty, or 20+ other integrations.
How IsDown Monitors AWS
IsDown checks AWS's status page every few minutes, across all 5,228 components. We combine official status data with user reports to detect when AWS is down, often before the vendor announces it.
When AWS status changes, IsDown sends alerts to your preferred channels. Filter by severity to skip noise and focus on outages that affect your business.

What you get when monitoring AWS with IsDown
Track AWS incidents and downtimes by severity
IsDown checks AWS official status page for major/minor outages or downtimes. A major outage is when AWS experiences a critical issue that severely affects one or more services/regions. A minor incident is when AWS experiences a small issue affecting a small percentage of its customer's applications. An example is the performance degradation of an application. The moment we detect a AWS outage, we send you an alert and update your dashboard and status page.
Get alerted as soon as users report problems with AWS
AWS and other vendors don't always report outages on time. IsDown collects user reports to provide early detection of outages. This way, even without an official status update, you can stay ahead of possible problems.
All the details of AWS outages and downtimes
IsDown collects all information from the outages published in AWS status page to provide the context of the outage. If available, we gather the title, description, time of the outage, status, and outage updates. Another important piece of information is the affected services/regions which we use to filter the notifications that impact your business.
Only get alerted on the AWS outages that impact your business
IsDown monitors AWS and all their 5228 components that can be affected by an outage. IsDown allows you to filter the notifications and status page alerts based on the components you care about. For example, you can choose which components or regions affect your business and filter out all other outages. This way you avoid alert fatigue in your team.
How IsDown Works
Get started in minutes. Monitor all your critical services from one place.
We monitor official status pages
IsDown checks the status of over 6,020+ services every few minutes. We aggregate official status information and normalize it, plus collect crowdsourced reports for early outage detection.
You get notified instantly
When we detect an incident or status change, you receive an alert immediately. Customize notifications by service, component, or severity to avoid alert fatigue.
Everything in one dashboard
View all your services in a unified dashboard or public or private status page. Send alerts to Slack, Teams, PagerDuty, Datadog, and 20+ other tools your team already uses.
No credit card required • 14-day free trial
AWS Downdetector vs IsDown
Looking for AWS outage alerts like Downdetector? IsDown monitors AWS's official status page for verified incident data, not just user reports. Know exactly when AWS is down, which components are affected, and when service health is restored. Here's why official AWS status monitoring beats crowdsourced detection:
| Features | IsDown | Downdetector |
|---|---|---|
| Official AWS status page monitoring. Know when AWS is down with real time incident details. | ||
| Monitor 6,020+ services including AWS in a single dashboard. | ||
| Instant AWS outage alerts sent to Slack, Teams, PagerDuty, and more. | ||
| Combined monitoring: AWS official status plus user reports for early outage detection. | ||
| Maintenance feed for AWS | ||
| Granular alerts filtering by AWS components and regions. |
14-day free trial • No credit card required
Frequently Asked Questions
Is AWS down today?
AWS is down. You can check AWS status and incident details on the top of the page. IsDown continuously monitors AWS official status page every few minutes. In the last 24 hours, there were 0 outages reported.
What is the current AWS status?
AWS seems to be having problems. You can check AWS status and incident details on the top of the page. The status is updated in almost real-time, and you can see the latest outages and issues affecting customers.
Is there a AWS outage now?
Yes, there is an ongoing outage. You can check the details on the top of the page.
Is AWS down today or just slow?
Yes, AWS might be slow as there's an ongoing outage. You can check the details on the top of the page.
How are AWS outages detected?
IsDown monitors the AWS official status page every few minutes. We also get reports from users like you. If there are enough reports about an outage, we'll show it on the top of the page.
Is AWS having an outage right now?
AWS last outage was on March 07, 2026 with the title "Increased Error Rates - Zurich"
How often does AWS go down?
IsDown has tracked 389 AWS incidents since May 2020. When AWS goes down, incidents typically resolve within 143 minutes.
Is AWS down for everyone or just me?
Check the AWS status at the top of this page. IsDown combines official status page data with user reports to show whether AWS is down for everyone or if the issue is on your end.
What AWS components does IsDown monitor?
IsDown monitors 5228 AWS components in real-time, tracking the official status page for outages, degraded performance, and scheduled maintenance.
How to check if AWS is down?
- Subscribe (if possible) to updates on the official status page.
- Create an account in IsDown. Start monitoring AWS and get alerts in real-time when AWS has outages.
Why use IsDown to monitor AWS instead of the official status page?
Because IsDown is a status page aggregator, which means that we aggregate the status of multiple cloud services. You can monitor AWS and all the services that impact your business. Get a dashboard with the health of all services and status updates. Set up notifications via Slack, Datadog, PagerDuty, and more, when a service you monitor has issues or when maintenances are scheduled.
How IsDown compares to DownDetector when monitoring AWS?
IsDown and DownDetector help users determine if AWS is having problems. The big difference is that IsDown is a status page aggregator. IsDown monitors a service's official status page to give our customers a more reliable source of information instead of just relying on reports from users. The integration allows us to provide more details about AWS's Outages, like incident title, description, updates, and the parts of the affected service. Additionally, users can create internal status pages and set up notifications for all their third-party services.
Latest Articles from our Blog
Monitor AWS status and get alerts when it's down
14-day free trial · No credit card required · No code required
Get instant alerts when AWS goes down